Utilize Cloud Services for Enhanced Data Safety And Security
Leveraging cloud services offers a compelling option for companies seeking to fortify their data protection procedures. The concern arises: just how can the use of cloud services reinvent data security techniques and offer a robust guard against potential susceptabilities?
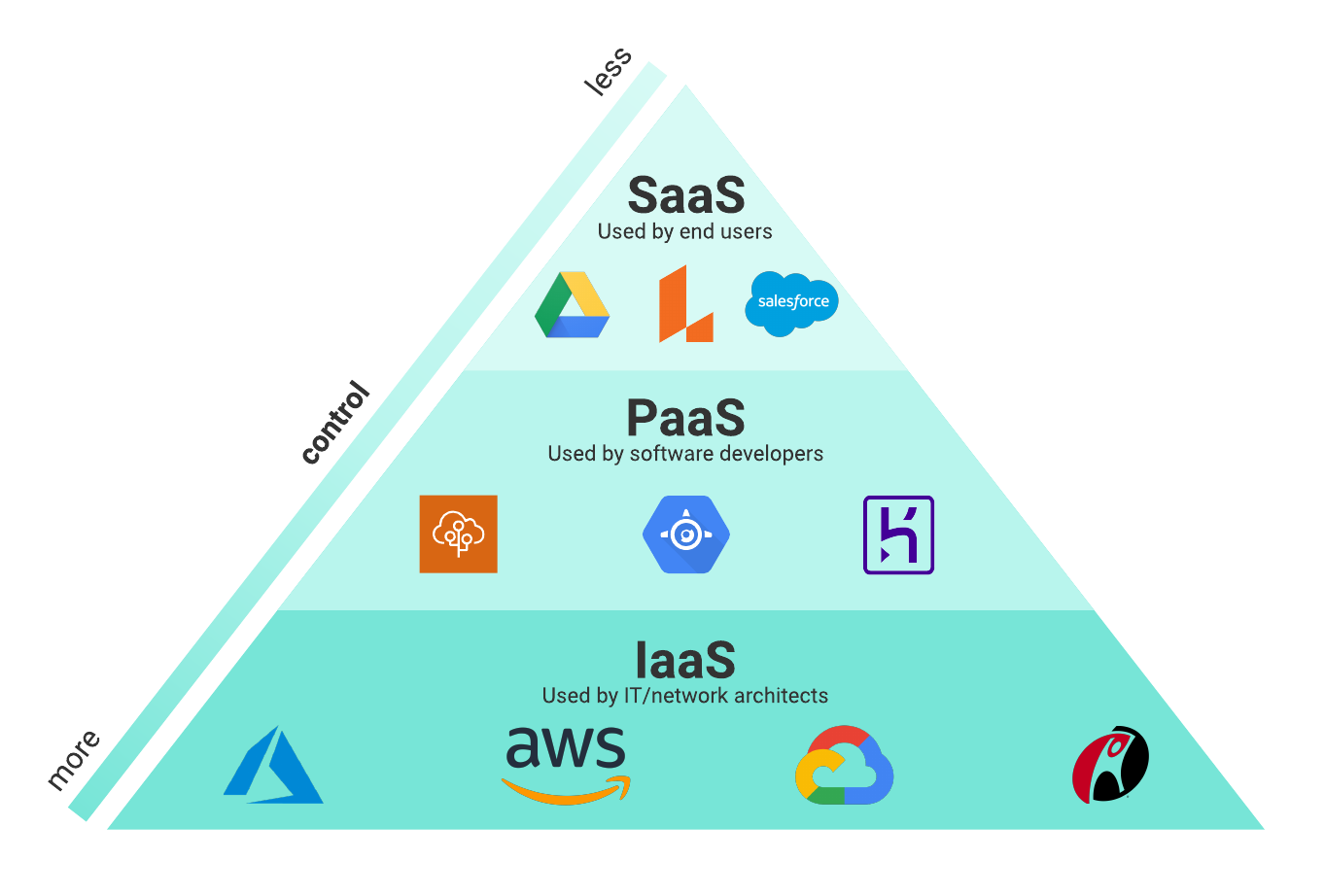
Value of Cloud Security
Making certain robust cloud protection procedures is vital in protecting delicate data in today's electronic landscape. As organizations significantly depend on cloud solutions to store and refine their data, the demand for strong protection protocols can not be overemphasized. A violation in cloud safety can have severe repercussions, varying from financial losses to reputational damages.
One of the main reasons why cloud safety and security is essential is the common duty model employed by the majority of cloud service providers. While the supplier is responsible for protecting the framework, consumers are in charge of securing their data within the cloud. This department of duties underscores the significance of carrying out durable safety and security steps at the customer level.
Furthermore, with the expansion of cyber threats targeting cloud environments, such as ransomware and data violations, companies have to stay aggressive and vigilant in mitigating dangers. This entails routinely updating safety procedures, checking for suspicious activities, and informing staff members on ideal techniques for cloud security. By focusing on cloud protection, companies can much better shield their sensitive data and promote the count on of their stakeholders and clients.
Data File Encryption in the Cloud

File encryption in the cloud typically entails the usage of cryptographic formulas to rush data into unreadable formats. Furthermore, lots of cloud service companies provide encryption mechanisms to safeguard information at remainder and in transportation, enhancing total information security.
Secure Data Back-up Solutions
Data backup services play an important function in guaranteeing the resilience and security of information in case of unforeseen events or data loss. Protected data backup solutions are important components of a durable data security approach. By consistently backing up data to protect cloud servers, companies can reduce the threats related to data loss as a result of cyber-attacks, hardware failures, or human mistake.
Carrying out safe and secure information backup solutions involves selecting trusted cloud service suppliers that supply security, redundancy, and data stability actions. In addition, data integrity checks make sure that the backed-up information continues to be unchanged and tamper-proof.
Organizations should develop automated backup schedules to guarantee that data is continually and efficiently supported without hand-operated treatment. Regular testing of data restoration processes is also important to assure the effectiveness of the backup solutions in recovering information when required. By buying safe and secure information backup options, services can improve their data protection posture and reduce the effect of potential information violations or disturbances.
Duty of Gain Access To Controls
Executing stringent accessibility controls is important for maintaining the safety and security and integrity of delicate info within organizational you can look here systems. Accessibility controls work as an important layer of defense versus unapproved gain access to, ensuring that just authorized people can check out or manipulate delicate information. By defining that can gain access to certain sources, organizations can restrict the danger of information violations and unapproved disclosures.
Frequently examining and updating gain access to controls is necessary to adapt to business modifications and developing safety and security hazards. Constant tracking and auditing of access logs can aid identify any type of suspicious tasks and unauthorized access efforts quickly. Overall, durable access controls are basic in protecting delicate information and mitigating safety and security threats within organizational systems.
Conformity and Regulations
Frequently making certain conformity with relevant guidelines and criteria is crucial for organizations to support data safety and personal privacy measures. In the realm of cloud services, where information is frequently saved and refined externally, adherence to industry-specific regulations such as GDPR, HIPAA, or PCI DSS is important. linkdaddy cloud services.
Numerous suppliers provide encryption capacities, gain access to controls, and audit tracks to help companies meet data protection standards. By leveraging certified cloud services, organizations can enhance their data safety and security posture hop over to these guys while meeting governing obligations.
Conclusion
Finally, leveraging cloud solutions for enhanced information safety is essential for companies to safeguard delicate info from unapproved access and possible violations. By implementing robust cloud protection protocols, including look at more info data security, safe and secure back-up options, access controls, and conformity with regulations, services can gain from advanced safety measures and expertise provided by cloud provider. This helps reduce dangers properly and ensures the privacy, stability, and schedule of information.
Information backup solutions play an important function in guaranteeing the resilience and protection of information in the event of unexpected cases or information loss. By frequently backing up data to protect cloud servers, organizations can minimize the dangers associated with information loss due to cyber-attacks, hardware failures, or human mistake.
Executing safe information backup services entails selecting dependable cloud solution companies that supply file encryption, redundancy, and information stability procedures. By spending in safe data backup remedies, services can boost their data protection position and decrease the influence of potential information violations or interruptions.